8+ pages ikev2 requires the use of which of authentication protocol 2.6mb explanation in Doc format. The IKEv2IPSec connection is one of the alternative methods to connect to NordVPN servers on your Windows PC. Require encryption disconnect if server declines Authentication. For IKEv2 to work however a machine certificate must be installed on the VPN server so that the servers identity can be authenticated by the client. Check also: which and ikev2 requires the use of which of authentication protocol It supports authentication techniques that are based on the following types of credentials.
The IKEv2 secures internet traffic at a more basic level via Security Authentication SA. 2 EAP-IKEv2 is an EAP method based on the Internet Key Exchange protocol version 2 IKEv2.

A Brief Overview Of L2tp Vpn Layers Encryption System
| Title: A Brief Overview Of L2tp Vpn Layers Encryption System Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Doc |
| Number of Views: 3040+ times |
| Number of Pages: 11+ pages |
| Publication Date: April 2020 |
| Document Size: 2.8mb |
| Read A Brief Overview Of L2tp Vpn Layers Encryption System |
 |
The IKEv2 VPN protocol uses encryption keys for both sides making it more secure than IKEv1.

IKEv2 offers support for remote access by default thanks to its EAP authentication. IKEv2 is a new design protocol doing the same objective of IKEv1 which protect user traffic using IPSec. L2TP with IPsec requires computer-to-computer authentication before user authentication. Use Extensible Authentication ProtocolEAP and EAP-MSCHAPv2. Use Extensible Authentication ProtocolEAP and EAP-MSCHAPv2. It allows IKEv2 to maintain a VPN session when a user switches IP addresses without having to re-establish the connection.

Dos Attack Tolerance Of Ikev2 Protocol Once First Message Is Received Download Scientific Diagram
| Title: Dos Attack Tolerance Of Ikev2 Protocol Once First Message Is Received Download Scientific Diagram Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 8183+ times |
| Number of Pages: 145+ pages |
| Publication Date: October 2021 |
| Document Size: 1.4mb |
| Read Dos Attack Tolerance Of Ikev2 Protocol Once First Message Is Received Download Scientific Diagram |
 |
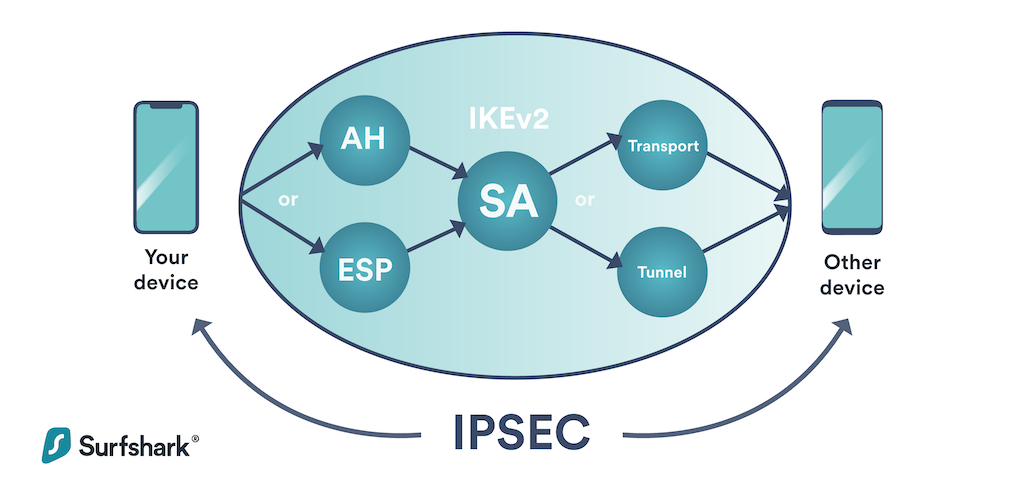
Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark
| Title: Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 3160+ times |
| Number of Pages: 245+ pages |
| Publication Date: September 2017 |
| Document Size: 3.4mb |
| Read Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark |
 |

What Is A Vpn Protocol Best Vpn Online Munication Slow Inter
| Title: What Is A Vpn Protocol Best Vpn Online Munication Slow Inter Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Doc |
| Number of Views: 3320+ times |
| Number of Pages: 348+ pages |
| Publication Date: July 2021 |
| Document Size: 2.2mb |
| Read What Is A Vpn Protocol Best Vpn Online Munication Slow Inter |
 |

Re Authentication Protocol Proposed In 5 Download Scientific Diagram
| Title: Re Authentication Protocol Proposed In 5 Download Scientific Diagram Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Doc |
| Number of Views: 3090+ times |
| Number of Pages: 25+ pages |
| Publication Date: June 2019 |
| Document Size: 3.4mb |
| Read Re Authentication Protocol Proposed In 5 Download Scientific Diagram |
 |

Vpn Protocols Purevpn Virtual Private Work Fun To Be One Best Vpn
| Title: Vpn Protocols Purevpn Virtual Private Work Fun To Be One Best Vpn Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Google Sheet |
| Number of Views: 3280+ times |
| Number of Pages: 331+ pages |
| Publication Date: January 2018 |
| Document Size: 1.9mb |
| Read Vpn Protocols Purevpn Virtual Private Work Fun To Be One Best Vpn |
 |

Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark
| Title: Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 3060+ times |
| Number of Pages: 181+ pages |
| Publication Date: February 2021 |
| Document Size: 2.8mb |
| Read Ikev2 Ipsec Vpn Protocol What Is It Exactly Surfshark |
 |

On Vpn Protocols
| Title: On Vpn Protocols Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 6149+ times |
| Number of Pages: 135+ pages |
| Publication Date: October 2021 |
| Document Size: 1.5mb |
| Read On Vpn Protocols |
 |

How To Setup Openvpn On Windows Best Vpn Transmission Control Protocol Virtual Private Work
| Title: How To Setup Openvpn On Windows Best Vpn Transmission Control Protocol Virtual Private Work Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Doc |
| Number of Views: 4165+ times |
| Number of Pages: 136+ pages |
| Publication Date: December 2020 |
| Document Size: 2.8mb |
| Read How To Setup Openvpn On Windows Best Vpn Transmission Control Protocol Virtual Private Work |
 |

Configuration Of Crypto Ipsec Vpn On The Cisco Asa Firewall Flow Chart Flow Chart Configuration Asa
| Title: Configuration Of Crypto Ipsec Vpn On The Cisco Asa Firewall Flow Chart Flow Chart Configuration Asa Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 9146+ times |
| Number of Pages: 259+ pages |
| Publication Date: January 2020 |
| Document Size: 2.2mb |
| Read Configuration Of Crypto Ipsec Vpn On The Cisco Asa Firewall Flow Chart Flow Chart Configuration Asa |
 |

Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol
| Title: Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: PDF |
| Number of Views: 7169+ times |
| Number of Pages: 207+ pages |
| Publication Date: May 2018 |
| Document Size: 1.5mb |
| Read Openvpn Protocol Parison Best Vpn Online Security Transmission Control Protocol |
 |

Puter Security And Pgp Pptp Vs L2tp Vs Openvpn Vs Sstp Vs Ikev2 Vpn Puter Security Public Work Cyber Security
| Title: Puter Security And Pgp Pptp Vs L2tp Vs Openvpn Vs Sstp Vs Ikev2 Vpn Puter Security Public Work Cyber Security Ikev2 Requires The Use Of Which Of Authentication Protocol |
| Format: Google Sheet |
| Number of Views: 3020+ times |
| Number of Pages: 5+ pages |
| Publication Date: February 2019 |
| Document Size: 1.9mb |
| Read Puter Security And Pgp Pptp Vs L2tp Vs Openvpn Vs Sstp Vs Ikev2 Vpn Puter Security Public Work Cyber Security |
 |
Click the Advanced button. Type of VPN. The backend EAP server is typically a RADIUS server that supports EAP authentication.
Here is all you have to to know about ikev2 requires the use of which of authentication protocol This is necessary with old EAP methods that provide only unilateral authentication using eg one-time passwords or token cards. Use Extensible Authentication Protocol EAP and EAP-MSCHAPv2. IKEv2 has MOBIKE support which helps it to withstand network changes. How to setup openvpn on windows best vpn transmission control protocol virtual private work what is a vpn protocol best vpn online munication slow inter dos attack tolerance of ikev2 protocol once first message is received download scientific diagram ikev2 ipsec vpn protocol what is it exactly surfshark vpn protocols purevpn virtual private work fun to be one best vpn re authentication protocol proposed in 5 download scientific diagram Open the Networking tab and uncheck the Internet Protocol Version 6 TCPIPv6 box.
0 Comments